Sometimes, we would like to prove if a specific file existed at sometime in filesystem, and then got deleted. That is, the received image doesn’t have the file we’re looking for.
Journaling
Filesystems have the concept of journaling which allows the OS to keep a track of changes that are made to the filesystem itself.
NTFS FileSystem
NTFS filesystem has two journal types
- USN Journal
Purpose: keep track of changes to files/directories in the filesystem with the reason of each and every change
Location: C:\$Extend\$USNJOURNAL
$USNJOURNAL contains both $MAX and $J files
What we’re mostly interested in is the $J file where a track of changes to files and folders are recorded - LogFile ($LOGFILE)
This file keeps a track of changes to $MFT file
Journals Parsing Tools
- ANJP
- MFTECMD
- etc.
Example Let’s check 2nd medium challenge (CopyPaSTe) in (incident-response-challenge.com) website and try to solve it.
Used tool here will be MFTECMD
MFTECMD used command
MFTECmd.exe -f "C:\Users\%username%\Downloads\Challenges\Medium - NTFS Journal Forensics - Copy PaSTe\Challenge\Artifacts-J\$J" --csv . --csvf J_CSV.csv
-f points to $J file
I’ve already downloaded the question evidence into my current Downloads folder.
–csv . means create csv file in the same current directory
–csvf means name the outputted csv file this way
5th Challenge
This challenges focuses on proving whether a specific file related to (John’s E-Mail data) has existed previously on Theon’s system.
Question Screenshot
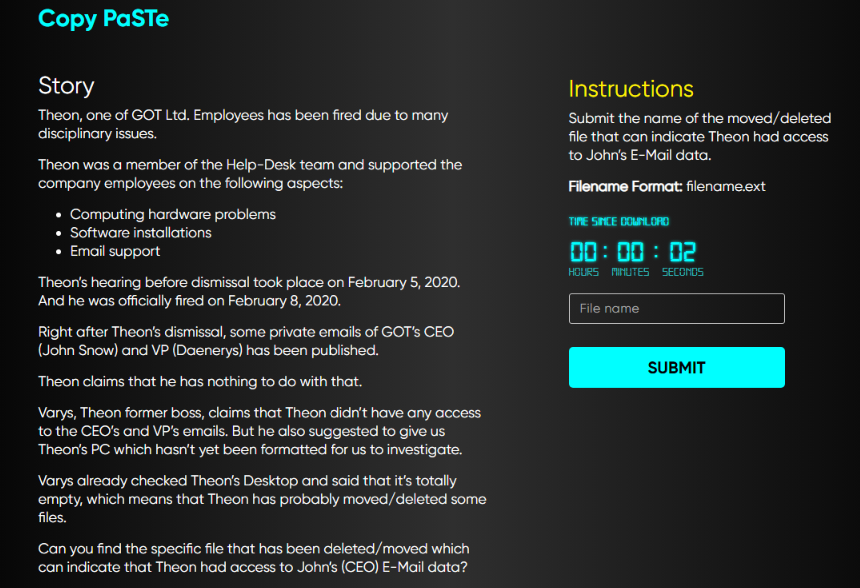
Since the question’s artifacts are only $MFT and Journaling files. We’ll parse $J using MFTECMD to find out if such a file existed on the system or not using the mentioned above command
As we can see in the outputted CSV file after some filtration to only include files that have the word “john”, the following entries are seen. Evidently, PST file was created and then deleted from the file system
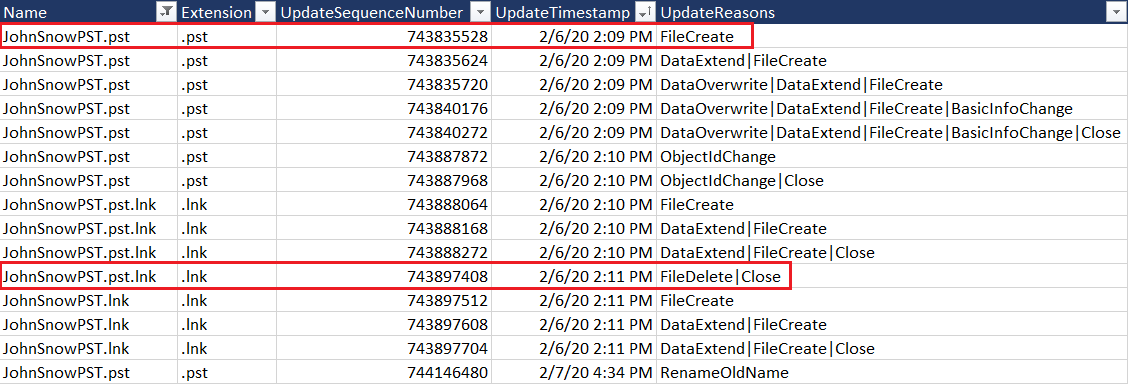
Answer to the challenge
File Name: JohnSnowPST.pst
References
- The challenge used in this post belongs to incident-response-challenge.com