In a digital forensics investigation, one of the important points to look for is lateral movement between systems in the environment. This post shows how to prove if there was lateral movement through Sysinternal PsExec tool using only Windows EventLogs as an evidence artifacts.
What is PsExec?
It’s a tool that lets you execute processes on other systems.
An example of PsExec executing commands remotely
Let’s say we want to open a CMD window on a remote system
psexec \\RemoteIP -u DomainName\UserName -p UserPassword cmd
Break it down
we have psexec already installed on our system, and we run it from CMD connecting to a RemoteIP system with a valid username/password there, and eventually start a CMD instance on the other system
How does PsExec execute commands remotely? Through interacting with Service Control Manager (SCM) via the network either through
- Remote Procedure Call (RPC) or
- Server Message Block (SMB).
PsExec Execution Steps (Example)
- Authentication completed on the target system
- An Administrative share is mapped
- PsExec service binary (PSEXESVC) is copied to the mapped share
- PsExec communicates with SCM via the network to start the service binary (PSEXESVC)
- Starts the intended process/application on the target system
PsExec Detection via EventLogs
Source System
- Security logs
- Event ID: 4688 (PsExec Process Creation)
- Event ID: 4689 (PsExec Process has been exited)
- Event ID: 4648
- Account Name(Under Subject section): the already logged on user on the source system
- Account Name (Under Account whose credentials were used section): the used account on the target system
- Target Server Name: target system
- Process Name: Used process (if no change to PsExec name, the executable info will have PsExec)
- Network Address: target IP
Target System
- System logs
- Event ID: 7045 (PSEXESVC was installed)
- Event ID: 7036 (PSEXESVC service state has changed)
- This event should appear twice once service has started (Executing state), and the second time when the service gets stopped (Stopped state)
- Security logs
- Event ID: 4624
- Successful logon
- Event ID: 4672
- Special privileges assigned to new logon
- Event ID: 5140
- A network share object was accessed
- Event ID: 5145
- A network share object was checked to see whether client can be granted desired access
- Event ID: 4656
- A handle to an object was requested
- Event ID: 4663
- An attempt was made to access an object
- Event ID: 4624
- Eventlogs Parsing/Viewing Tools
- EvtxEcmd
- Event Log Explorer
- Timeline Explorer
- etc.
Example Let’s check 4th medium challenge (Kiwi) in (incident-response-challenge.com) website and try to solve it.
Used tools here will be EvtxEcmd to parse eventlogs, and Timeline Explorer to view and filter eventlogs.
9th Challenge
This challenge tells an appearance of kiwi logo (Mimikatz) appeared on DESKTOP-HUB666E (172.16.44.135), this is probably due to lateral movement from other systems.
Provided evidence - DESKTOP-HUB666E eventlogs - WIN-IL7M7CC6UVU (DC) eventlogs
Challenge Questions
- Provide another domain user account used by attacker aside from King-Slayer
- Provide target system IP when this user was used
To solve this challenge, we’ll parse only Security and System eventlogs from the two systems provided eventlogs to detect if there is lateral movement occurred between them using PsExec
Parsing Steps for each machine
- Copy only Security and System eventlogs into a directory named Logs2, for example.
- Run EvtxECmd on each directory as mentioned below
EvtxEcmd used command
DESKTOP-HUB666E (172.16.44.135)
EvtxECmd.exe -d "C:\Users\%username%\Downloads\Challenges\Medium - PassTheHash - Event Logs - Kiwi\Challenge\KingSlayerHost- EventLogs\Logs2" --csv . --csvf KingSlayerHost.csv
DC (WIN-IL7M7CC6UVU) (172.16.44.132)
EvtxECmd.exe -d "C:\Users\%username%\Downloads\Challenges\Medium - PassTheHash - Event Logs - Kiwi\Challenge\DC-EventLogs\Logs2" --csv . --csvf DC.csv
Let’s view the two file logs using Timeline Explorer
To determine source of lateral movement we will use the mentioned event IDs 4688,4689, and 4648 looking for PsExec in them
This event “4648” shows the execution of PsExec on Feb 9
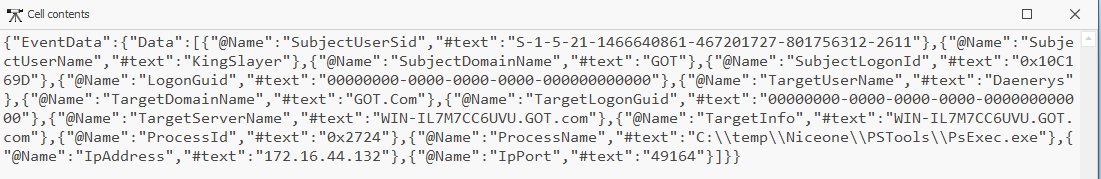
Event time: 2020-02-09 13:59:13
To break the event into what we know
Subject Account Name: KingSlayer (Already logged on user)
Target User name: Daenerys (User account which will be used on the target system)
Target Server Name: WIN-IL7M7CC6UVU
Process Name: C:\temp\Niceone\PSTools\PsExec.exe
Target IP Address: 172.16.44.132
Answer to the challenge
IP address of target machine: 172.16.44.132
Username: Daenerys
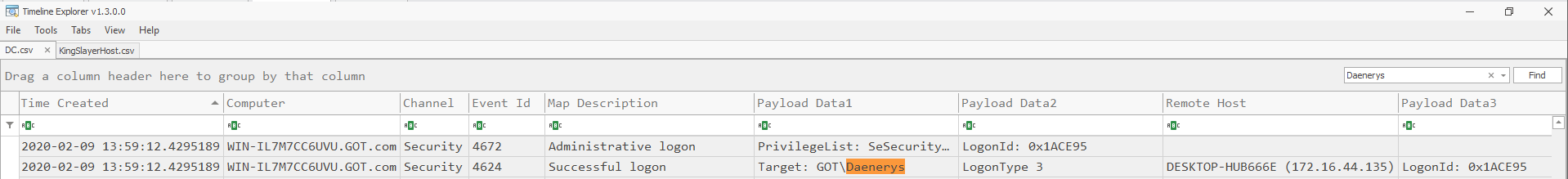
Evidence from destination system
Security logs, Event IDs: 4624 & 4672
Used pivot point: Daenerys
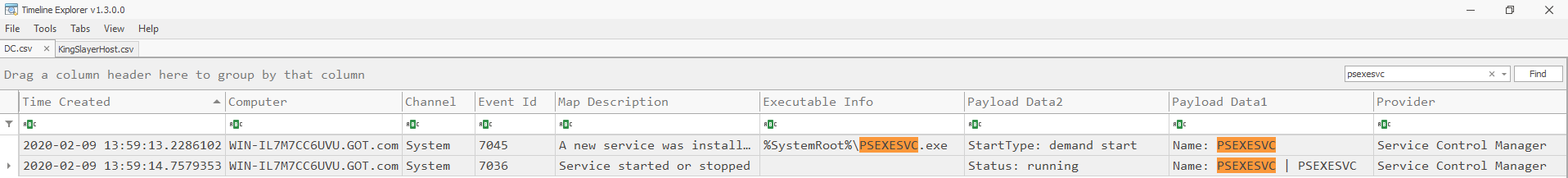
System logs, Event IDs: 7045 & 7036
Used pivot point: PSEXESVC
Note
In this example PSEXESVC service name wasn’t changed from default. This can be changed; however, using -r option once executing PsExec in the source system.
References
- The challenge used in this post belongs to incident-response-challenge.com
- https://www.jpcert.or.jp/english/pub/sr/20170612ac-ir_research_en.pdf
- https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventID=4648
- https://docs.microsoft.com/en-us/sysinternals/downloads/psexec