What is Windows Management Instrumentation (WMI)?
TL;DR
WMI is a feature which allows querying, collecting, and managing Windows OS components eihter locally or remotely
A bit Longer Definition
WMI is a Microsoft implementation of Web-Based Enterprise Management (WBEM) in Windows OS
What is WBEM?
- It is an open standard called the Web-Based Enterprise Management (WBEM) which aims to exchange Comon Information Model (CIM) data between systems
What is CIM?- It is a data model standard which allows hardware, Operating Systems or applications for example to define classes that represent the different components they have. An example would be a class that represents information about hardisk
Example
I would like to know the details about services on my system, and in specific DHCP service. I would write the following powershell command
Get-CimInstance -Namespace root/CIMV2 -ClassName CIM_Service | Where-Object {$_.Name -eq "dhcp"}
With WMI, we are able to have powerful tasks gets accomplished such as creating processes remotely.
How is WMI organized?
It is organized into Namespaces > Classes > Instances
Essentially, namespace may contain different classes, and classes can have one or more instances.
This is clear in the previous example, another example where there is one instance for this class
Get-CimInstance -Namespace root/CIMV2 -ClassName Win32_OperatingSystem
output is the OS instance information
How does WMI provide us info about the operating system? This could be understood by looking at WMI architecture
WMI Architecture
WMI consists of 3 components:
- WMI Providers & Managed Objects
So for any component to have its information available via WMI. It needs to have a provider which handles requests and queries about this object- Providers consist of two components which are
- DLL File
- Managed Object Format (MOF)
- CIM scripts which describe classes that are available in WMI repository.
- Providers consist of two components which are
- WMI Infrastructure
- WMI core (WMI service) and WMI repository (C:\Windows\System32\wbem\repository)
- WMI Consumers
These are basically what can query WMI repository such as- Powershell
- WMIC (WMI command-line utility)
- Programming languages such as C#, C++, VB, etc.
How to access WMI repository?
Using one of two protocols which are
- Distributed Component Object Model (DCOM)
- First, What is COM?
COM is a standard which specifies how objects or components can interact with other components whether they are in the same process or in different processes on the same computer
- What is DCOM?
DCOM is the idea of having components or objects interact with other components even if they are in different systems
For a component to request a service from another component in another system, this request can be forwarded to Remote Procedure Call (RPC) protocol which acts as the transmission protocol
- First, What is COM?
- WinRM
- WinRM is Microsoft implementation of protocol called WSMAN.
- What is WSMAN?
It is a messaging protocol for exchanging information between a server and a client. It often relies on HTTP.
- What is WSMAN?
- WinRM is Microsoft implementation of protocol called WSMAN.
WMI Attacks
WMI can be leveraged by attackers in several post exploitation phases
- Reconnaissance
- Privilege Escalation
- Lateral Movement
- Persistence
I will explain with examples how WMI is used in only the latter two phases: Lateral movement & Persistence
In addition, I’ll explain approaches to detect them
WMI Lateral Movement
Two examples to perform lateral movement using WMI are
- wmi process call create
- wmiexec.py
This is a fileless lateral movement, no need for the existence of any file on the target system, WMI will achieve the task
Communication will appear over port TCP 135 in the beginning, and then later a random port will be used after negotiation succeeds between the two systems
WMI Lateral Movement Detection Example
Scenario
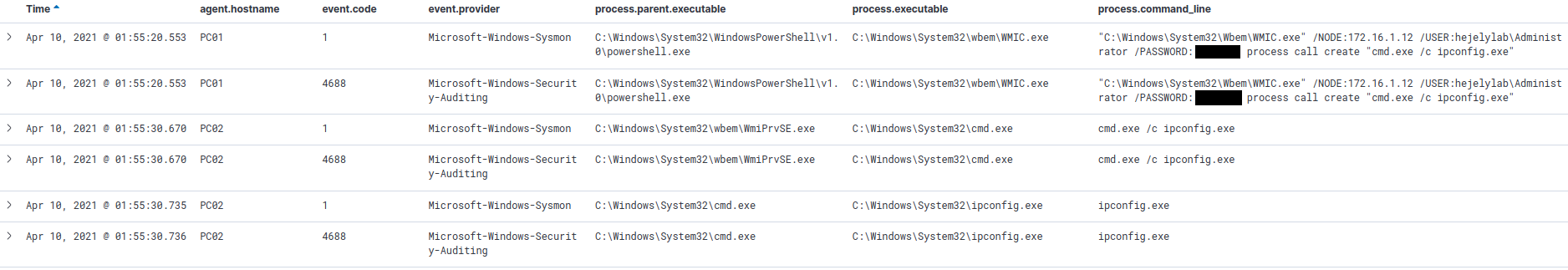
- In this example we will run “CMD /c ipconfig.exe” on remote system using WMIC command line utility, and confirm the observed events in both source and target systems.
-
Used WMIC command
wmic.exe /NODE:172.16.1.12 /USER:"hejelylab\Administrator" /PASSWORD:"UserPassword" process call create "cmd.exe /c ipconfig.exe" - Eventlogs
- Security Event logs
You need to have Command Line Auditing Enabled. No logs appeared to me in this example if command line logging is not enabled and sysmon is not installed.- Source
- Security logs, event ID: 4688
- Process name: WMIC.exe
- Parent process name: powershell.exe
- Security logs, event ID: 4688
- Target
- Security logs, event ID: 4688
- Process name: cmd.exe
- Parent process name: WmiPrvSE.exe
- Security logs, event ID: 4688
- Process name: ipconfig.exe
- Parent process name: cmd.exe
- Security logs, event ID: 4688
- Source
- Sysmon Event logs
- Source
- Sysmon logs, event ID: 1
- Process name: WMIC.exe
- Parent process name: powershell.exe
- Sysmon logs, event ID: 1
- Target
- Sysmon logs, event ID: 1
- Process name: cmd.exe
- Parent process name: WmiPrvSE.exe
- Sysmon logs, event ID: 1
- Process name: ipconfig.exe
- Parent process name: cmd.exe
- Sysmon logs, event ID: 1
- Source
- Security Event logs
WMI Persistence
WMI persistence can be achieved via WMI event subscription for example
Steps:
- An MOF file gets created
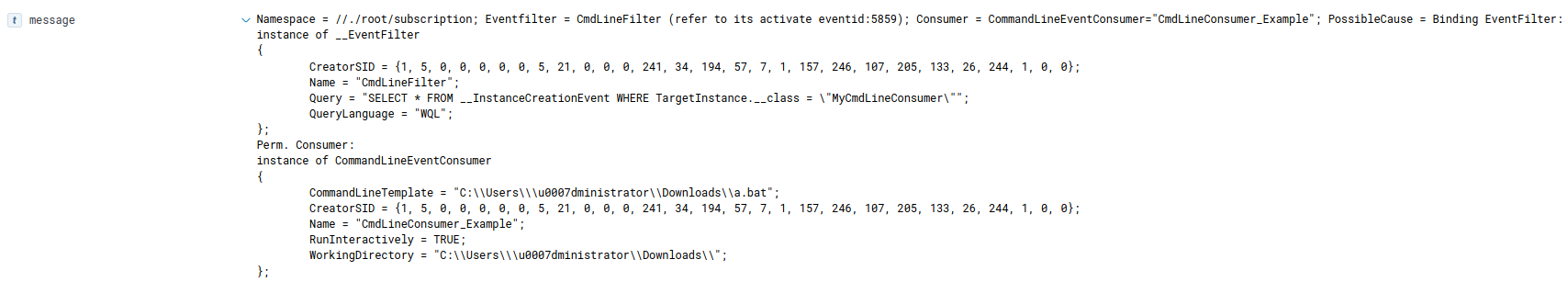
- MOF file contains the following:
- Event Trigger (Class __EventFilter)
- An example, event trigger is a specific date, an event that occurs on the system (notepad.exe starts)
- Event Consumer (Class __EventConsumer)
- What will happen once the trigger occurs, for example, run a specific script command.
- Binding (class __FilterToConsumerBinding)
- This what binds the consumer to the trigger.
- Event Trigger (Class __EventFilter)
- Compile MOF file
- Using mofcomp.exe
Persistence is achieved!!!
WMI Persistence Detection Examples
First Example
Scenario
- A MOF file is dropped to system
- The MOF file gets compiled using mofcomp.exe (mofcomp is spawned by powershell)
WMI event consumer event is executed (The example here is to run BATCH script which will execute cmd)
Detection
- Sysmon
- Event ID 1: powershell > mofcomp.exe .\a.mof
- Event ID 20: WmiConsumerEvent
- Event ID 21: WmiBindingEvent
- WMI-Activity Operational Log
- Event ID 5861: records permanent event consumer creation
- Event ID 5861: records permanent event consumer creation
- Security
- Event ID 4688: powershell > mofcomp.exe .\a.mof
All events in one table
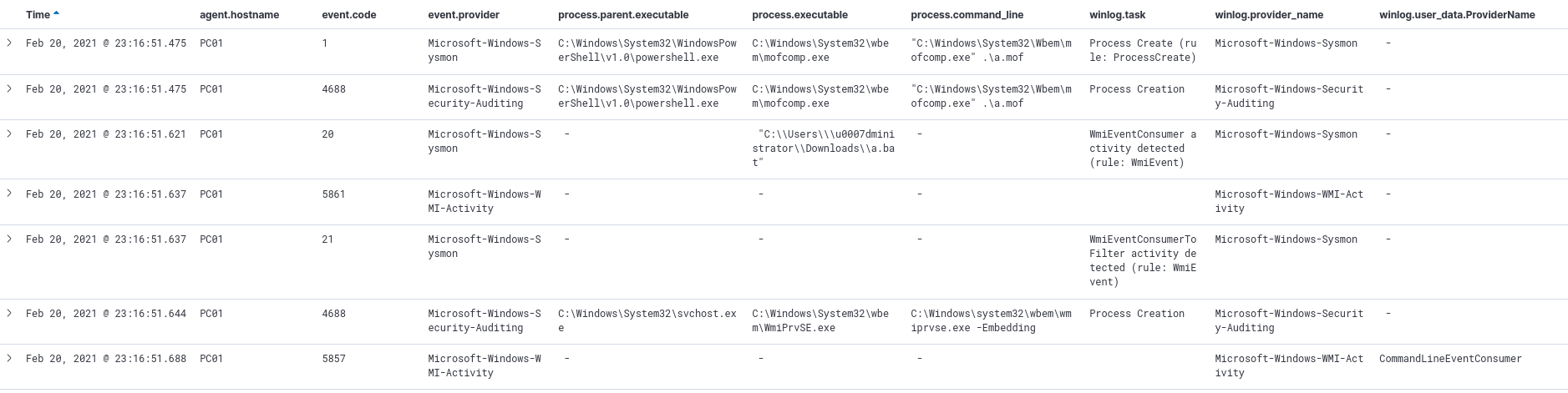
Note (Different example): Sysmon also triggers for WMI event filter in Event ID: 19.
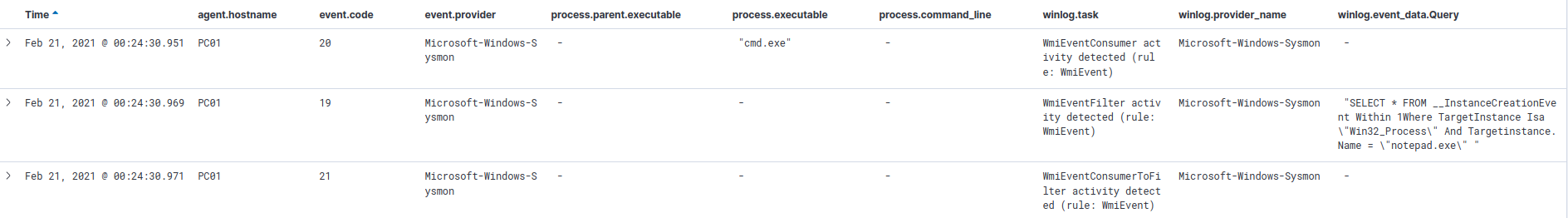
Second Example,WMI detection using WMI
I will compile the following MOF file in advance to view valid results of WMI detection using WMI
Executed command: mofcomp.exe .\LogonTime.mof
LogonTime.mof
-
Purpose: After being compile, for any interactive logon “LogonType=2”, CMD will be run and echo date and time into “C:\Users\administrator\Downloads\LogonTime.txt”
-
LogonTime.mof Content
#pragma namespace (“\\.\root\subscription”)
instance of __EventFilter as $FILTER
{
Name = “VBScript Filter”;
EventNamespace = “root\cimv2”;
Query = “SELECT * FROM __InstanceCreationEvent WITHIN 5 WHERE (TargetInstance ISA ‘Win32_LogonSession’ AND (TargetInstance.LogonType = 2))”;
QueryLanguage = “WQL”;
};
instance of ActiveScriptEventConsumer as $CONSUMER
{
Name = “VBScript CMD Consumer”;
ScriptingEngine = “VBScript”;
ScriptText = “Set objShell = CreateObject("WScript.Shell")\n” “objShell.Run "C:\Windows\system32\cmd.exe /C echo %date%%time% > C:\Users\administrator\Downloads\LogonTime.txt"\n”;
};
instance of __FilterToConsumerBinding
{
Consumer = $CONSUMER ;
Filter = $FILTER ;
};
Once logging out and logging again interactively, ipconfig will be executed.
Remember that MOF contains
- trigger filter (__EventFilter),
- consumer (__EventConsumer), and
- Binding (__FilterToConsumerBinding)
We can fetch this infomation using the following powershell cmdlets
Get-CimInstance -Namespace root/subscription -ClassName __EventFilter
Get-CimInstance -Namespace root/subscription -ClassName __EventConsumer

Get-CimInstance -Namespace root/subscription -ClassName __FilterToConsumerBinding
Third Example
- WMI Repository file
- File Name: OBJECTS.DAT
- Location: C:\Windows\System32\wbem\Repository
- Purpose: this file contains WMI executed commands on system. We can pull it andexamine it
I wrote an example of how to do this in this post WMI Persistence Example
References
- https://www.varonis.com/blog/wmi-windows-management-instrumentation/
- https://www.fireeye.de/content/dam/fireeye-www/global/en/current-threats/pdfs/wp-windows-management-instrumentation.pdf
- https://www.youtube.com/watch?v=aBQ1vEjK6v4
- https://pentestlab.blog/2020/01/21/persistence-wmi-event-subscription/
- https://www.hackingarticles.in/lateral-movement-wmi/
- https://medium.com/threatpunter/detecting-removing-wmi-persistence-60ccbb7dff96